In response to the increasing trend of cyber threats, the Department of Defense (DoD) recently implemented a new cybersecurity standard for contractors who work with the US Military Services to be assured that its vendors are adequately securing their confidential data. In one of the biggest-ever changes to Defense contracting, the Cybersecurity Maturity Model Certification or CMMC now requires contractors to go through three tiers of network security controls that will need to be checked by third-party assessors. Getting a CMMC Assessment will now be an added cost that contractors in the Defense sector have to bear and only those who provide commercial off-the-shelf products or services will be exempt.
The Cybersecurity Maturity Model Certification combines certifications into a unified cybersecurity standard and will assess the maturity of an organization’s cyber risk mitigation practices. Defense Industrial Base (DIB) partners as well as contractors are required to meet the DoD’s new CMMC guidelines to bid on future projects.
How did the change in CMMC requirements come about?
The USA loses a whopping USD 6 Billion a year to adversaries due to exfiltration, data rights, and R&D losses. With robust cybersecurity protocols in place, the loss may be reduced by 10% or more, money better utilized by reinvesting in partners in the industrial base to give the country a competitive edge. In other words, the changes in requirements are a reflection of the Pentagon’s endeavors to protect defense industrial base networks and control unclassified information from cyber attacks.
What do the CMMC 2.0 rules entail?
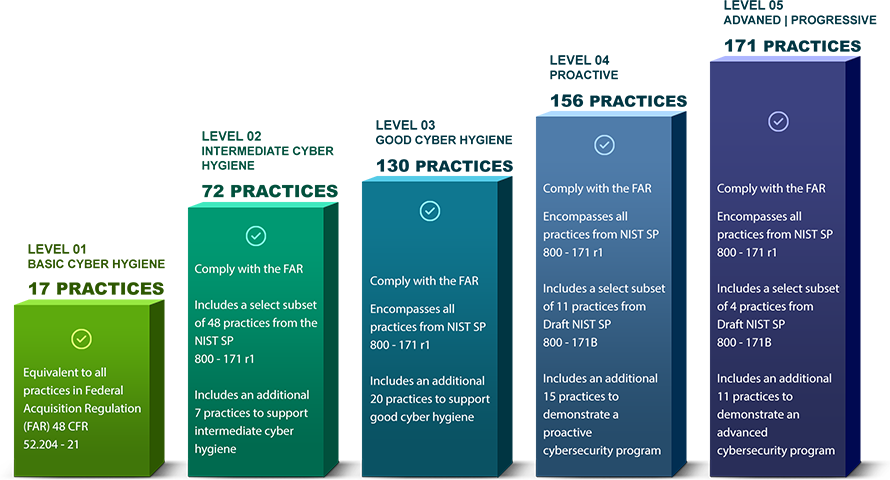
The CMMC 2.0 model, announced on July 17, 2021, has replaced the previous five-tier system with three levels: Foundational (Level 1), Advanced (Level 2), and Expert (Level 3). The required assessment for CMMC certification varies depending on the level selected.
CMMC rules will require contractors to be certified by third-party auditors to ensure that companies are adhering to certain standards. Organizations will be required to meet different levels of security, with level one being the lowest (foundational) and level three being the most stringent (expert, proactive, and advanced cyber practices). Each level consists of practices and processes that a contractor must follow if he wishes to achieve that level of certification.
The three levels correlate to the following:
- CMMC Level 1 – Safeguard Federal Contract Information (FCI)
- CMMC Level 2 – Serve as a transition step between Level 1 and 3 in cybersecurity maturity progression to protect CUI
- CMMC Level 3 – Protect Uncontrolled, Unclassified Information (CUI)
Levels 4 and 5, which have now been discontinued focussed on the protection of CUI and reduction in the risk of Advanced Persistent Threats (APTs)
To adequately prepare, an organization will need to do the following:
- Do Readiness Assessment and Gap Analysis
- Create a Remediation Plan
- Monitor and Report on findings
- Prepare a System Security Plan (SSP)
Learn more about the external assessment required by CMMC 2.0 on our blog or join a cybersecurity webinar.
How SureShield Can Help
Looking to streamline your IT risk assessment framework?
ComplyShield by SureShield is an essential compliance management tool that helps organizations navigate and achieve compliance with the CMMC 2.0 model. With the updated CMMC levels, including Foundational (Level 1), Advanced (Level 2), and Expert (Level 3), ComplyShield provides the necessary guidance and support at each stage.
ComplyShield allows users to select their targeted CMMC level and efficiently manages the compliance process from start to finish. The platform provides step-by-step guidance for certification readiness, ensuring organizations meet the specific requirements of each CMMC level. This automated compliance solution can be used to conduct a readiness assessment and gap analysis based on the CMMC framework, identify gaps, and provide a remediation plan with associated reporting and output the System Security Plan that will be required for certification.
Follow us on LinkedIn and Twitter to stay in the loop of new updates to compliance frameworks.