Complete Control
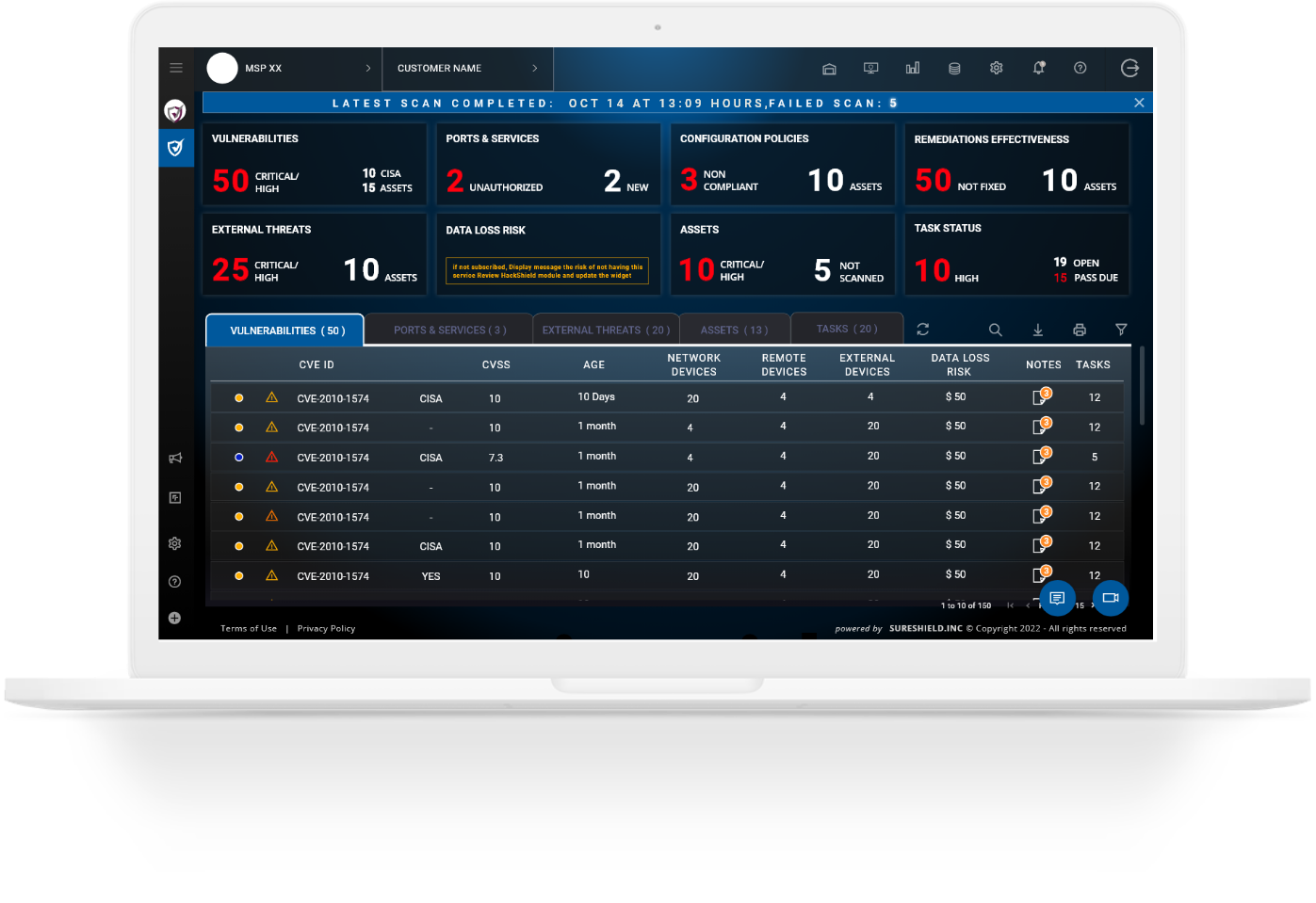
Achieve complete control over IT vulnerabilities and confidential data from anywhere, anytime. SecurityShield allows for easy deployment and customization to fit your monitoring and remediation processes.
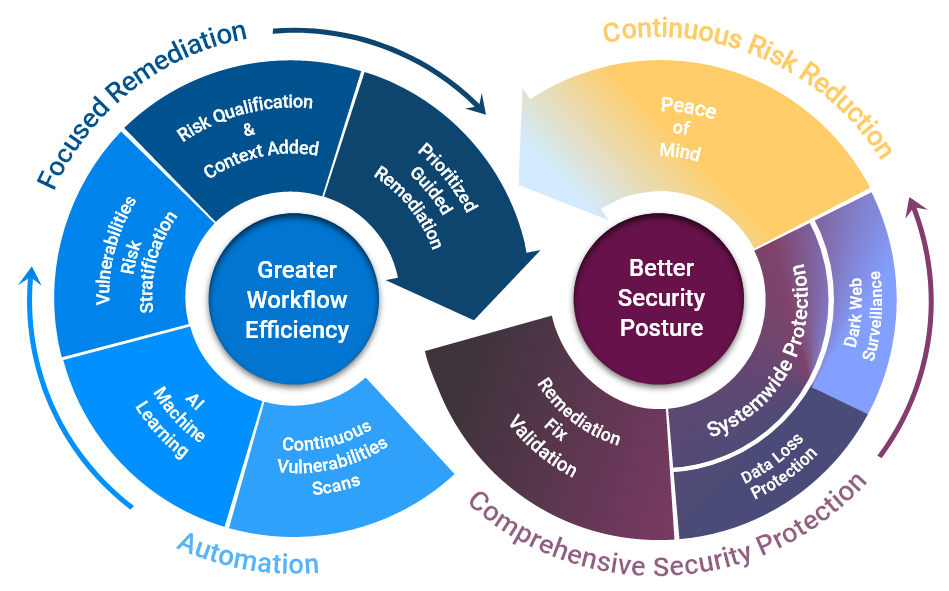
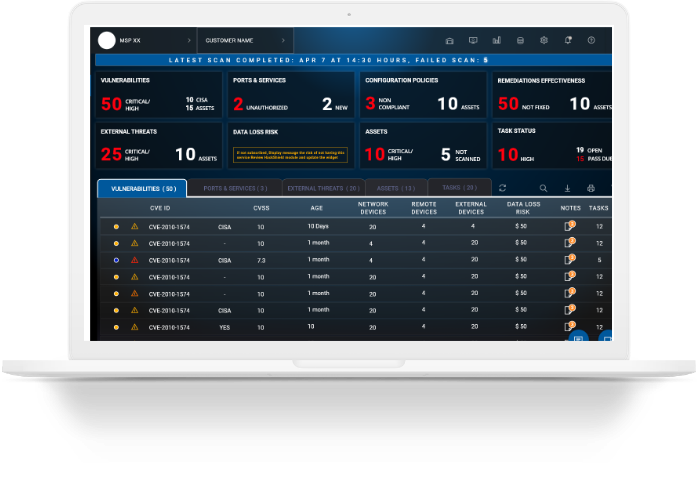
Designed for easy use, SecurityShield empowers IT security teams to track, manage and build a robust security posture.
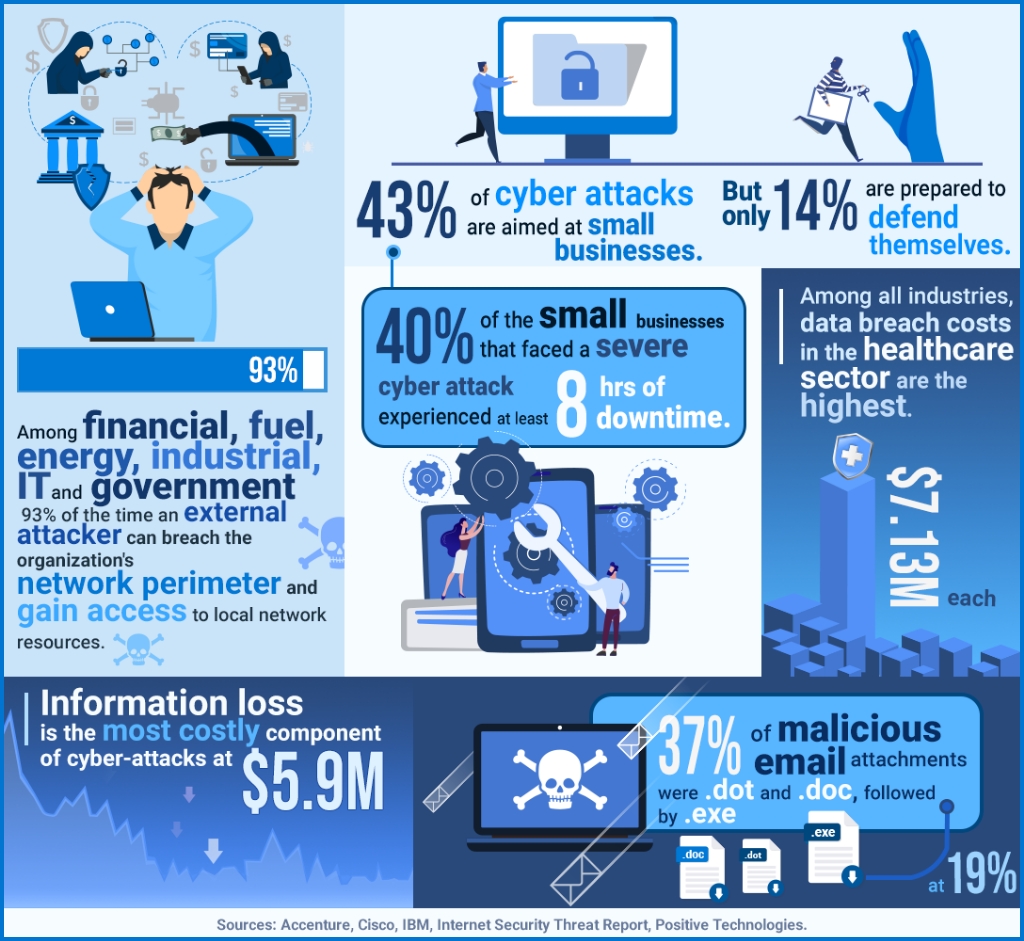
Our vulnerability detection capability is the gold standard in scanning technology. Compare SureShield output versus any other system; you are safer with us.